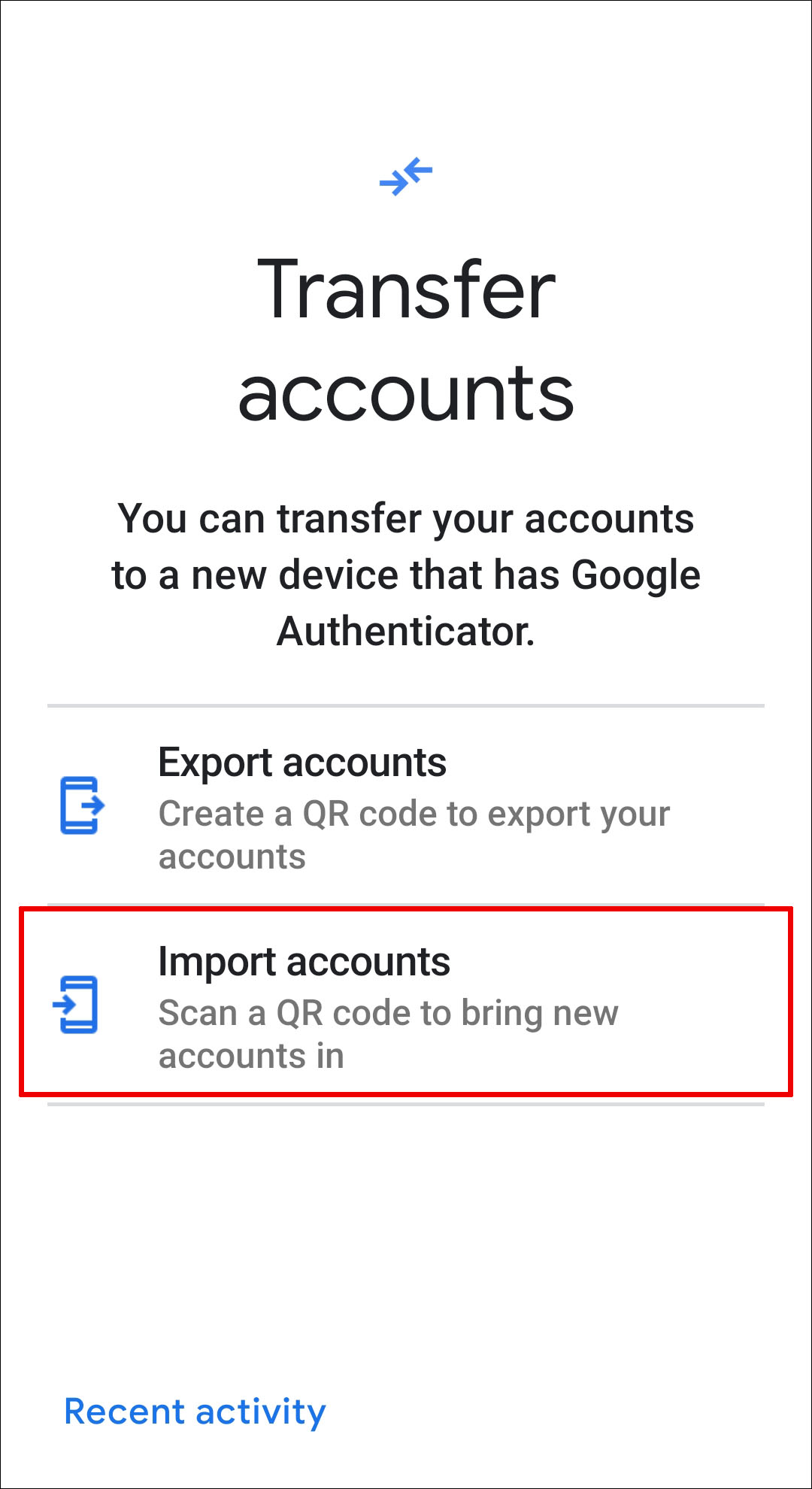
Latest version
- Google Authenticator Browser
- Google Authenticator Barcode
- Google Authenticator Desktop
- Google Authenticator Pc
Released:
A HOTP/TOTP code generator for the command line.
- Overall: Google Authenticator is a great platform to protect my personal information from my Google account and to allow me to generate a higher level of security for my account in general, either to access my email or to access my cloud storage. Google Authenticator allows me to generate a 6-digit code every 30 seconds, which is really.
- Google Authenticator is a software-based authenticator by Google that implements two-step verification services using the Time-based One-time Password Algorithm (TOTP; specified in RFC 6238) and HMAC-based One-time Password algorithm (HOTP; specified in RFC 4226), for authenticating users of software applications.
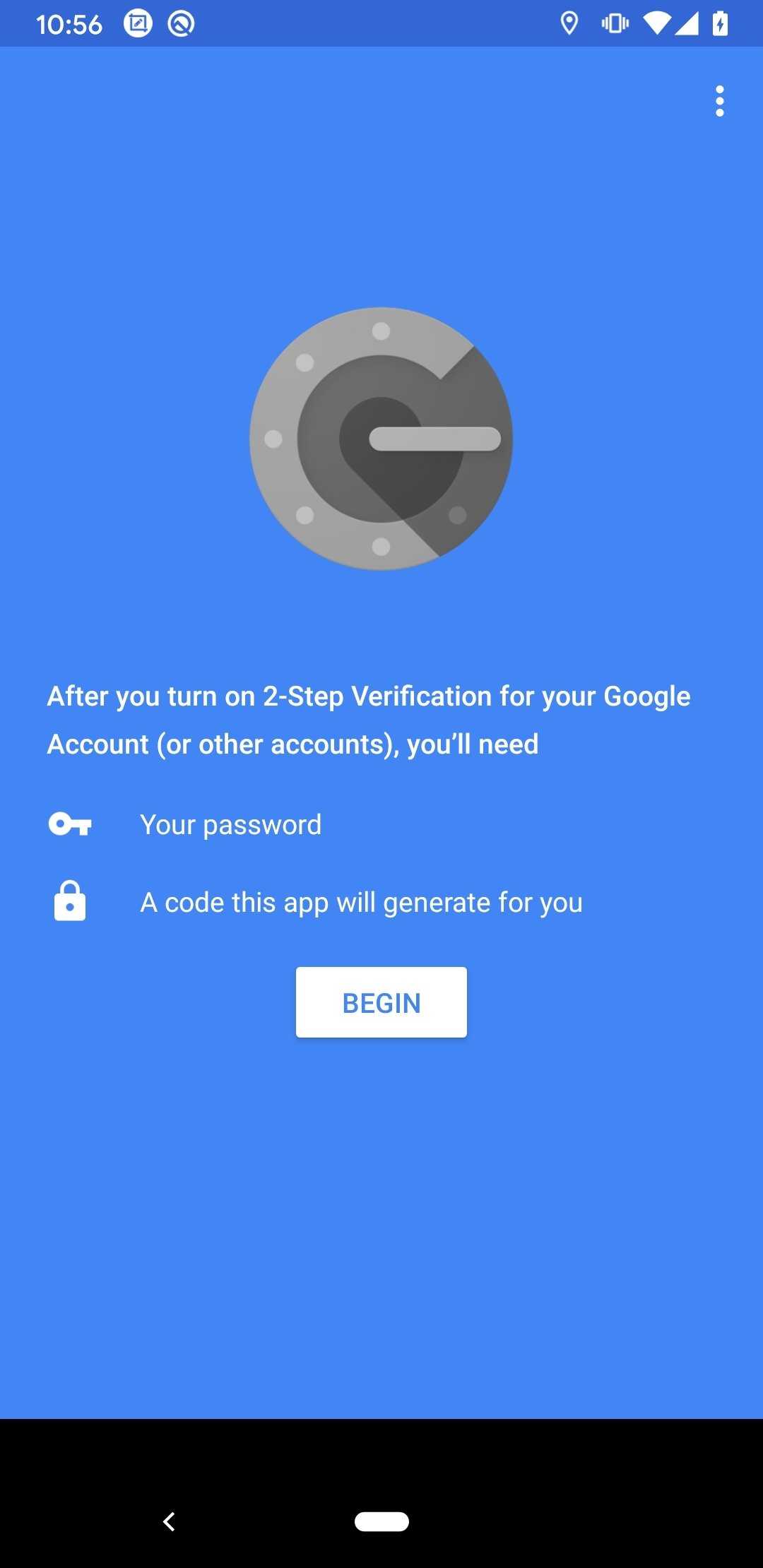
- Scan the QR code displayed on Google's website with the Authenticator app, then enter the six-digit code to verify everything is working properly. Once that's done, the codes on your old device.
Authenticator is a CLI analog to the Google Authenticator phone app, or the LastPass Authenticator phone app. It is a TOTP/HOTP client that can generate the numeric codes needed for authentication with sites that support Two-Factor Authentication (TFA) or Multi-Factor Authentication (MFA). Google Authenticator can issue codes for multiple accounts from the same mobile device. Each Google Account needs a different secret key. To set up extra accounts: Turn on 2-Step Verification for each account. Learn more about 2-Step Verification. Use the same Google Authenticator app.
Project description
authenticator is a CLI analog to the Google Authenticator phone app, or the LastPass Authenticator phone app. It is a TOTP/HOTP client that can generate the numeric codes needed for authentication with sites that support Two-Factor Authentication (TFA) or Multi-Factor Authentication (MFA).
Benefit
The benefit of using authenticator over a phone app is that this CLI utility can run anywhere Python 3.5 can run from a command line interface (e.g., a terminal window), and the database of accounts and secrets is a platform-independent passphrase-protected encrypted file that can be backed up and can be copied to multiple systems without fear of bad actors gaining access to the second factor authentication.
Another benefit is that authenticator can act as a backup in case you loose your phone or tablet (running Google Authenticator) or Google breaks the app or withdraws it.
Personally, I use both Google Authenticator on my iPhone and iPad, and run authenticator on several different computer systems. I keep a copy of the accounts file in a variety of places. If my phone bricks, is lost or stolen, I can still get access to my TFA-protected accounts if I can access any of those other computers, or any other computer on which I can install and run authenticator and access a copy of my accounts file.
Authentication secret (READ THIS)
TFA/MFA clients that produce a ‘one time’ numeric code require a secret that they share with the server validating the authentication. Typically this secret is generated by the server and captured by the client in the form of a QR code that can be scanned by the client app on your phone.
But this CLI utility doesn’t have the ability to capture or process QR images. It needs the secret in the form of a text string. If the server cannot provide a text string equivalent of the shared secret then you cannot use authenticator to generate one-time codes for that account.
Each account will use a different secret, a different text string. If you are already using a phone app to generate one-time TFA codes for some accounts then you’ll need to generate new secrets for those accounts (and update the info in the phone app) so that you can capture the secret as a text string.
GMail TFA example
If you enable Two-Factor Authentication for GMail, you’ll go through a setup process that first configures your account to send your phone a code by text or voice. At the end of the setup you’ll have an opportunity to add Google Authenticator as an alternative code generator. Select that and scan the QR code with your phone’s Authenticator app (Google Authenticator, LastPass Authenticator, et cetera). Then click the link labeled “CAN’T SCAN IT” under the QR code … that will give you a 32-character secret string that you’ll use to add configure this account in authenticator.
It is important that you capture the QR code and then click the link for the secret string secret code. If you capture the secret and click “back” to get the QR code then a new secret will be generated and the new QR won’t match the previously captured secret string. (With Google Authenticator you actually don’t need the QR code; you can also provide the secret as a text string using the ‘manual entry’ option when adding an account to the app. LastPass Authenticator doesn’t have that option.)
You add the account and secret to authenticator like so:
You then generate codes like so (use Ctrl-C to stop the generation):
System Requirements
This requires Python 3.5 or later.
It has been tested on OS X 11.9.5, Windows 10, and Ubuntu 14.04. As none of those systems come with Python 3.5 out of the box, you’ll need to install that yourself.
And I recommend setting up a Python 3.5 virtual environment in which to install authenticator.
Usage
Add an account
To add a new account, do something like:
You can use any string there as the name. I recommend the format ‘vendor:userid’, where vendor is some string indicating the organization or server that will check your TFA credentials, and userid is the user account id that is being authenticated.
You’ll get prompted for the passphrase to unlock the file in which all the account secrets are stored. And then you’ll get prompted for a secret string.
Generate current codes
To get the current code for all the accounts, do:
You’ll get prompted for the passphrase, and then the program will start generating the current passcode for all the accounts. It will continue to generate current codes every 5 seconds until you stop it with ctrl-C.
Other commands and options
There’s a lot more, just enter authenticator --help for a list of all the commands and something like authenticator add --help for detailed help on a specific command.
Implementation details
This is a simple attempt to implement the “Pseudocode for Time OTP”and “Pseudocode for Event/Counter OTP” given in the Wikipedia article on Google Authenticator. That pseudocode is reproduced here …
Pseudocode for Event/Counter OTP
I’ve validated the pseudocode and this implementation against RFC6238 (TOTP), RFC4226 (HOTP) and RFC4648 (Base32 encoding).
Dependencies
This implementation requires:
- Python 3.5 or later
Development
To setup the development environment on OS X, clone the repo from GitHub, and then cd in Terminal to the root of the cloned repository and do:
- dev/venv/make-venv.sh
- . dev/venv/activate-project.src
- dev/venv/provision-venv.sh
- dev/lint.sh
- dev/runtests.sh
To setup the development environment on OS X, clone the repo from GitHub, and then cd in Terminal to the root of the cloned repository and do:
- dev/venv/make-venv.ps1
- dev/venv/activate-project.ps1
- dev/venv/provision-venv.ps1
- dev/lint.ps1
- dev/runtests.ps1
You can find out more about why the virtual environment is setup and managed that way by looking at these blog posts:
I build the distribution using dev/build/make-package.sh.
Project details
Release historyRelease notifications | RSS feed
1.1.3
1.1.2
1.1.1
Download files
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/22496196/instauth.jpg)
Download the file for your platform. If you're not sure which to choose, learn more about installing packages.
Google Authenticator Browser
| Filename, size | File type | Python version | Upload date | Hashes |
|---|---|---|---|---|
| Filename, size authenticator-1.1.3-py3-none-any.whl (31.3 kB) | File type Wheel | Python version py3 | Upload date | Hashes |
| Filename, size authenticator-1.1.3.tar.gz (26.7 kB) | File type Source | Python version None | Upload date | Hashes |
Hashes for authenticator-1.1.3-py3-none-any.whl
| Algorithm | Hash digest |
|---|---|
| SHA256 | 9157175b6e104ee861df9c577d4f00953c37ead3f5ae145746ce4e470100aa3f |
| MD5 | 6e9b290736c9730d819bb15a0071bafa |
| BLAKE2-256 | b568f486848654b38021d6264291afcb3a97b23c41b9f5b7822bb3e7beb7f784 |
Hashes for authenticator-1.1.3.tar.gz
| Algorithm | Hash digest |
|---|---|
| SHA256 | 30b7a84a6983fd9f4b7f91df835ae853e901d301a33a38958f69d9da3c0eba33 |
| MD5 | ebd44760add52b46a3e83d19dfa3d3df |
| BLAKE2-256 | 1d8f35b612ab82a5a409898b05479b5bcc085790bcf9da9001c502ba7e718117 |
Do you know Google Authenticator? I hope you do, because it is really key to increase security for your Google account.
Google Authenticator Barcode

You can read more about it on Wikipedia or on Google website. Anyway it is really good way to secure your other services as well. For instance LastPass is using Google Authenticator to two-step authentication, which will allow you to increase security of your WordPress. You can even install WordPress Plugin called Google Authenticator. I was using it for one week but I removed it after all - it was exaggeration IMHO.
Google Authenticator Desktop
Anyway - I was fighting with Internet because I didn’t know how to remove certain “account” from application.
Google Authenticator Pc
In short words you just need to hold on account you want to remove and click on bin.